IPv6 at Home (Part II – Configuration)
In this article Im going to show on how to configure the Cisco ASA and the Cisco 1700 Router to have IPv6 connectivity at home and also gonna explain on why I had to use an ASA and a Router.
As written in the first article, my ISP does not offer IPv6 to its (private) customers, so to get IPv6 at home I had to use an IPv6 Tunnelbroker which is providing the IPv6 connectivity over a an 6in4 Tunnel. And that’s also the reason why an ASA without a router will not work in that scenario, its plain and simple, ASAs do not support tunnel Interfaces today..
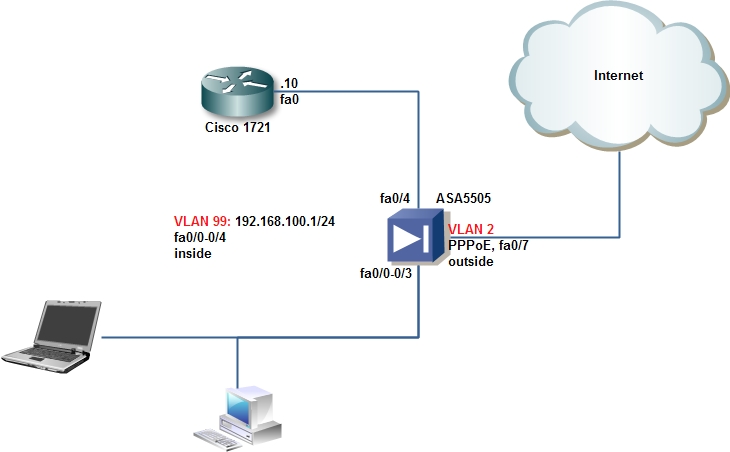
This is the network layout I use at home. There are other options but its how I did it 😉
The router is directly attached to the ASA on the inside:
interface FastEthernet0 ip address 192.168.100.10 255.255.255.0 speed auto ! ip route 0.0.0.0 0.0.0.0 192.168.100.1
The next part on the router is to configure the tunnel interface. I did interchange some parts of the IPv6 tunnel address with xx, just so save myself some trouble 😉
interface Tunnel10 description to HE IPv6 Tunnel Broker no ip address ipv6 address 2001:470:xx:xx::2/64 ipv6 enable tunnel source 192.168.100.10 tunnel destination 216.66.80.98 tunnel mode ipv6ip
The tunnel itself does not need an IPv4 address but the IPv6 address I got assigned from HE (remember the last post), IPv6 has to be enabled on the interface (ipv6 enable) and the Tunnel needs to be set to ipv6ip (tunnel mode ipv6ip). Using that tunnel mode means, that the IPv6 packets will be encapsulated into IPv4 to be passed over the IPv4 Internet.Thats the tunnel part on the router, now the ASA has to be configured so the tunnel packets get passed through.
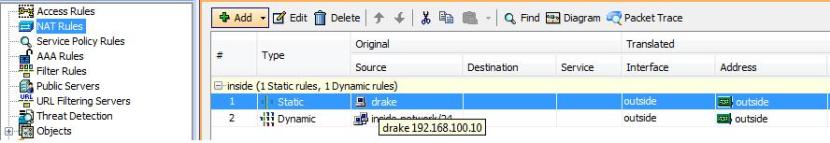
One thing that did cost me some time is the NAT part on the ASA. Usualy the ASA does dynamic NATing based on the UDP/TCP ports from the protocols I use from my home network to the internet. But since the IPv6IP Tunnel is Layer 3 (exactly its IP protocol nr. 41, IPv6 encapsulation) it is not going to use TCP or UDP ports. So what I had to do is to create a static NAT entry which is going to NAT all traffic from my router to the outside
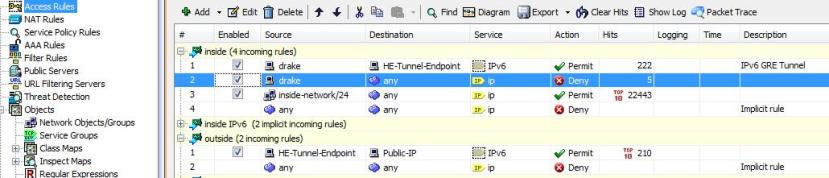
Next, the Firewall Rules have to be configured for the access:
Basically, the first two rules are not needed due to rule 3. But to get a small increase of security, I did first allow the IPv6 Tunnel from my router to the HE-Tunnel-Endpoint and then denied everything else from the router. Just in case some one gets into the router.
The important part is at the bottom of the picture, the incoming rule on the outside interface. The IPv6 Tunnel packets from the HE-Tunnel-Endpoint have to be permitted, which tells me, that the ASA is not statefull on Layer 3 😉
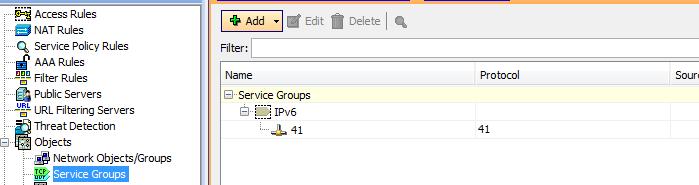
The Service object IPv6 is a Service Group I created with IP protocol nr 41
So if I did not forget something, the connectivity to the HE-Tunnel-Endpoint should be working now:
drake#ping 2001:470:xx:xx::1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:470:xx:xx::1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 8/11/12 ms
Now to get back on the IPv6 connectivity inside the home network, the router needs some additional configuration.
ipv6 unicast-routing ! interface FastEthernet0 ip address 192.168.100.10 255.255.255.0 speed auto ipv6 address 2001:470:xx::1/64 ipv6 enable ! ipv6 route ::/0 2001:470:xx:xx::1
As of today, IPv6 Routing has to be enabled (ipv6 unicast-routing) , before the router will route 😉
To get my home network into the IPv6 Cloud, I enabled IPv6 on the inside interface with a /64 part of my routable /48 network which is the default gateway for my end PCs and Notebooks. And last but not least the default route to the HE-Tunnel-Endpoint so my packets actually get somewhere.
Now I only had to activate IPv6 on my PC, give it an address and configure the DNS Server address which I got from HE. Thats it, I can go now to ipv6.google.ch 😉
hehe ok before I finish, we gotta talk about security, at least a bit. Even though IPv6 is not wide spread today, its still the big bad internet with a lot of bad people. And with the configuration so far, the Tunnel is wide open, which also counts to the devices behind. A small negative point since all my addresses are global ones..
So I’ve just built a small firewall configuration with ip inspect and an access-list on the router:
ipv6 inspect name IPv6 tcp ipv6 inspect name IPv6 udp ipv6 inspect name IPv6 icmp ! interface Tunnel10 description to HE IPv6 Tunnel Broker no ip address ipv6 address 2001:470:xx:xx::2/64 ipv6 enable ipv6 traffic-filter IPv6-IN in ipv6 inspect IPv6 out tunnel source 192.168.100.10 tunnel destination 216.66.80.98 tunnel mode ipv6ip ! ipv6 access-list IPv6-IN deny ipv6 any any
Basically this firewall is doing the same thing as the ASA does for IPv4, allow everything from the inside network and block everything from the outside.
A nice gotcha is how to activate the IPv6 access-list on the interface: ipv6 traffic-filter, thank you Cisco! Why cant it be ipv6 access-group, as in IPv4 😉
So thats it, thanks for reading and I hope it did help
Since the ASA can only match either TCP, UDP, or (all) IP within a static statement that is bound to a single IP address (as is the base case with most residential ISP circuits), the ASA can no longer respond on that address with other services (e.g. an IPsec tunnel endpoint). This is because all connections (which don’t match other static or dynamic translations) will be translated to the internal router, instead of being handled by the ASA.
Are you doing anything to work around this?
Just read part III. Nevermind.
hehe yes, that’s why I had to change the whole set up. I did not find a workaround for it with only one public IP. In the end, its easier anyway with the router in front of the ASA 🙂
I was just too lazy at that time to change everything again…
In case anyone stumbles across this down the road, this is how I got it working with a single ip on the ASA:
Define an object for each end of the tunnel:
object network IPV6ROUTER
host 192.168.99.254
object network HE-ENDPOINT
host 209.51.161.14
Allow protocol 41:
access-list FIREWALL extended permit 41 any any (yes, I was lazy)
And as much as I abhor the new way of doing NAT on the ASA…. it’s what made this possible:
nat (inside,outside) source static IPV6ROUTER interface destination static HE-ENDPOINT HE-ENDPOINT
Hi Kevin
Thanks for the followup, hope I get some time (somewhen) to test this 🙂